Prelude
Pandora was an easy machine from HTB, developed by TheCyberGeek & dmw0ng. This was an easy box and it demonstrated the importance of manual enumeration and the importance of accuracy in scan results.
For the foothold, we have to do an snmpwalk output to get credentials of a low privilged user. We can use this credential to login via SSH as daniel. Once we are in as daniel, we can find an instance of Pandora FMS running as user matt. We can then exploit an authentication bypass vuln in Pandora FMS to gain shell as matt.
After getting shell as matt, we can use a simple Path Injection vulnerabilty of a custom SUID binary to be root.
Let me elaborate on how I solved this box.
Exploitation
Nmap returned the following results.
Nmap scan report for 10.10.11.136
Host is up (0.053s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Play | Landing
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 115E49F9A03BB97DEB840A3FE185434C
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelI navigated to port 80 and found the following web page.

I’ve tried several types of enumerations (Full port scan, UDP scan, Vhost brute forcing etc.), but didn’t found anything interesting.
That’s when I’ve decided to perform a UDP scan once again with nmap, but this time with a lower T value and to scan only the top 500 ports. I used -T3 for the scanning.
nmap -sU -v --top-ports=500 -T3 10.10.11.136This scan was taking some time to run.
While UDP scan was running, I’ve checked if port 161 was open and found it was indeed open!
nmap -sU -p 161 10.10.11.136

I’ve ran snmpwalk with the following syntax.
snmpwalk -Os -c public -v 2c 10.10.11.136|tee snmpwalk In the output, I’ve found an interesting commandline argument, where credentials to a user named daniel was given as an inline argument.

I’ve tested these credentials against SSH for credential reuse and it got me in!
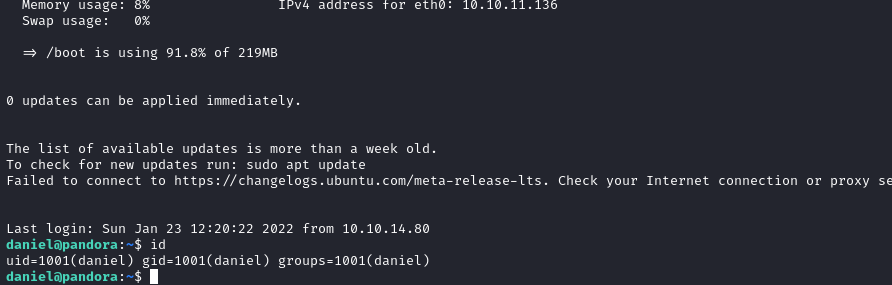
Privilege Escalation #1
The user.txt flag was not present in daniel‘s home directory. It was present in /home/matt.
So, the next step is to escalate privileges to matt
I’ve started some local recon and Navigated to /var/www and found a folder named pandora_console.
I’ve also found the apache configuration for pandora at /etc/apache2/sites-available and the contents of the file are listed below.

This configuration shows that an instance of Pandora FMS is running locally at the target and it can be accessed at localhost:80. I’ve checked with ps aux and found that pandora is running as user matt!
I’ve navigated to the website and found the following page.

I’ve searched for some exploits and found it had some interesting ones!
I’ve found an authentication bypass vulnerability in Pandora FMS.
If we can get admin access in Pandora FMS, then we could potentially upload a malicious PHP extension and gain code execution.
I’ve requested the following payload and refreshed the home page of Pandora FMS and I was logged in as admin!
http://localhost:8000/pandora_console/include/chart_generator.php?session_id=%27%20union%20SELECT%201,2,%27id_usuario|s:5:%22admin%22;%27%20as%20data%20--%20SgGO

Then I’ve zipped a malicous reverse shell PHP file and uploaded it as an Extension, via the Extension uploader.

After uploading the extension, I’ve clicked on Extension Manager view to execute the PHP code.
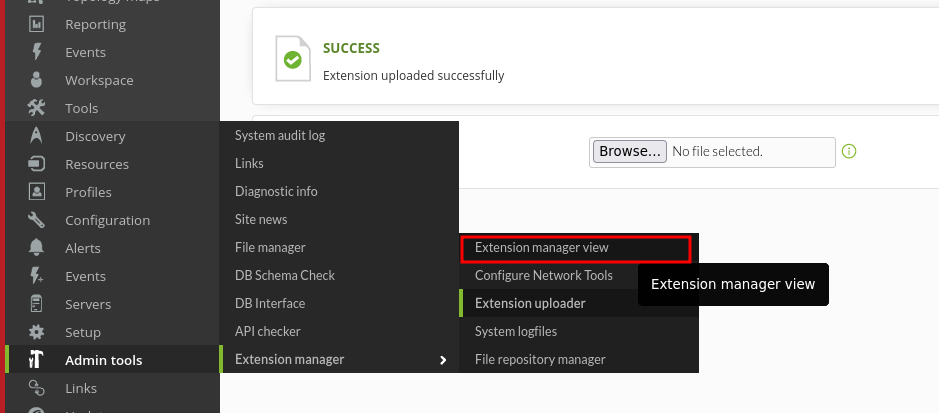
And I’ve got a shell back as matt!

Privilege Escalation #2
With some digging around the file system, I’ve found an interesting custom SUID binary with the source code next to it at /opt.

It was a custom backup utility, which backuped the contents of /var/www/pandora/pandora_console to a sub-directory inside the /root folder. The binary issues the tar command without the absolute path, so we could use Path hijacking attack to gain root.

However, upon running the binary, it showed that permission denied for accessing the /root folder. I’ve also noticed that I couldn’t run sudo -l as matt because of some weirdness of the reverse shell.
So, I had to spawn an SSH session as matt user, by writing an authorized_keys file first, to execute the SUID binary properly.
Once I had an SSH session as matt, I’ve used the Path hijacking attack to gain a shell as root!


Postlude
And that was Pandora.
An easy box, but taught me some good lessons!
Kudos to TheCyberGeek & dmw0ng.
Peace out! ✌️